Who we are
In line with the mission of Fondazione Bruno Kessler (FBK), which aims to achieve scientific research of excellence and have an impact on society, the Security & Trust Research Unit of the Center for Cybersecurity of FBK develops cutting-edge security solutions in the following areas:
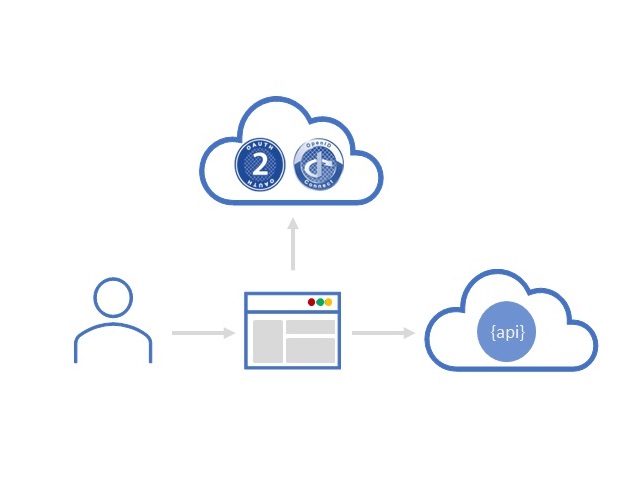
- Identity and Access Management (e.g., on-boarding, single and multi-factor authentication, access delegation, authorization and access control)
- Legal compliance (e.g., privacy and e-payment provisions)
- Complex and Heterogeneous systems (e.g., API, Cloud, Mobile, IoT and Blockchain)